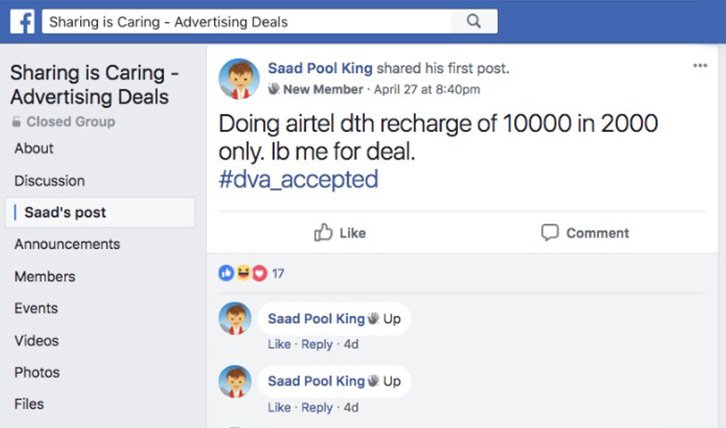
A security bug in the website of Airtel has allowed many bypasses the payment page and recharge digital TV (DTH) of worth thousands of rupees.
The incident came to light via a Facebook page ‘Saad Pool King’ which claimed to recharge DTH of worth Rs 10,000 charging a mere Rs 2,000. The people, who used the illegal method, paid the aforementioned amount using Paytm and UPI.
Entrackr has independently confirmed this with multiple users.
We also spoke to many who recharged Airtel DTH directly from the website leveraging the bug. While those were not very tech-savvy approached the Facebook page and get their recharge done.
The Facebook post garnered various positive comments from people who wanted to take the service. While some, who were hesitant, the handle clarified there is no risk in it as the information will not reach to Airtel.
The page also clarified it is using Burp Suite, a graphical tool for testing web application security, for the recharge service.
It appears the recharge amount goes in crores from the size of people who benefited from the bug.
The free DTH recharge service has, however, stopped and the Facebook page has also stopped responding to requests.
This is not the first time when a company has fallen victim to such bugs and lost millions.
In 2015, a similar case came to light when a security bug in the popular Bengaluru-based Ola Cabs service allowed hackers to enjoy unlimited free cab rides.
Last year, an Indian security engineer alerted Uber by pointing out a bug in the system that would allow anyone to take unlimited free rides. Uber, in turn, rewarded the white hacker with $5,000.